Third Party Risk Management Isn't One-Size-Fits-All

The infamous SolarWinds attack of December 2020 is often viewed and studied as a supply chain attack. However, since SolarWinds is a third-party provider of software products, the attack must also be considered from a “third-party risk” perspective.
By embedding malicious code into the SolarWinds Orion platform, hackers managed to access and compromise the IT systems of 250+ victim organizations. Thus, by attacking a single third party (SolarWinds), they were able to compromise many of their customers.
The SolarWinds event is a crucial reminder of why organizations need third-party risk management (TPRM). This article explores this need and highlights why organizations should avoid a one-size-fits-all TPRM approach.
What Is Third-party Risk Management?
TPRM is an aspect of enterprise risk management (ERM), albeit with a narrower focus to identify, assess, and reduce the risks arising from third parties. Examples of third parties include:
- Vendors
- Suppliers
- Outsourcing partners
- Contractors
- Government agencies
- Franchises
- Service or solutions providers (e.g., SolarWinds)
TPRM is sometimes known as vendor risk management (VRM). However, they are not the same.
Gartner defines VRM as a process to ensure that “the use of service providers and IT suppliers does not create an unacceptable potential for business disruption or a negative impact on business performance” for the organization.
In simple terms, VRM is about vetting third-party vendors and ensuring that working with them won’t negatively affect the organization. These consequences could be:
- Financial
- Reputational
- Operational
- Regulatory
VRM is also about mitigating cybersecurity risks arising from vendors and preventing malware-based and other types of cyberattacks and data breaches.
A third-party risk management program is about managing the risks arising from all third parties, not just vendors. As the organization grows and matures, a VRM program may be insufficient for comprehensively managing third-party risk. Here’s where TPRM comes in.
Why Do Organizations Need TPRM?
Most modern organizations have a complex supply chain consisting of multiple third parties that help business operations run smoothly, reduce costs, create economies of scale, and positively impact profits.
At the same time, third parties also introduce a fair measure of risk into an organization’s operational landscape, especially if they have access to the organization’s business-critical systems or sensitive data.
For instance, a vendor with weak cybersecurity controls increases the potential and cost of a data breach. Case in point: In 2020, the average cost of a data breach was $3.92 million, but breaches involving third parties cost $370,000 more.
In addition to information security and cybersecurity risk, third parties also expose your company to other kinds of risks, including:
- Financial
- Credit
- Legal
- Compliance
- Transactional and operational
- Strategic
If any of these risks are realized, they could impact the organization’s earnings, result in regulatory fines or legal action, and damage its reputation. To effectively manage and mitigate these risks, organizations need TPRM.
A formal, documented, and dynamic TPRM program enables organizations to:
- Identify all the third parties they use
- Evaluate how they use these third parties
- Assess if these third parties have adequate safeguards in place to protect the organization from various kinds of risk
That said, every organization needs a TPRM program tailored to its unique risk profile, risk tolerance, third-party ecosystem, and business objectives. That’s why TPRM is not a one-size-fits-all approach or strategy. The following section explores why.
The Challenges of TPRM (and Why TPRM Is Not a “One-Size-Fits-All” Strategy)
Organizations often incorporate commonly-accepted TPRM best practices into their TPRM program. And yet, a “cookie-cutter approach” to TPRM rarely works. Here’s why.
Every Organization Is Unique
With TPRM, what works for one organization may not work for another because every organization:
- Uses different third parties
- Has varying risk exposure from these third parties
- Has unique strategic, operational, financial, and competitive goals
Further, every organization may experience a different impact and probability of each risk, so they need a tailored TPRM program to identify, assess, prioritize, and mitigate risk.
The best TPRM programs show how TPRM teams can enhance third-party relationships and set up reliable procedures for due diligence, vendor reviews, and vendor controls.
Businesses should carefully assess how all their third parties access their systems and data. They should also evaluate if third parties access sensitive data and verify if these entities have implemented protective controls to protect the organization’s assets.
There are no readymade “templates” for these activities. Organizations need to set up their TPRM based on a thorough assessment of their own needs and vendor ecosystem.
TPRM Frameworks Are Helpful – but Only Up to a Point
Depending on the third-party ecosystem, setting up a TPRM program can be complex and time-consuming. Organizations can start with an industry-accepted TPRM framework to simplify and speed up the effort. Examples include:
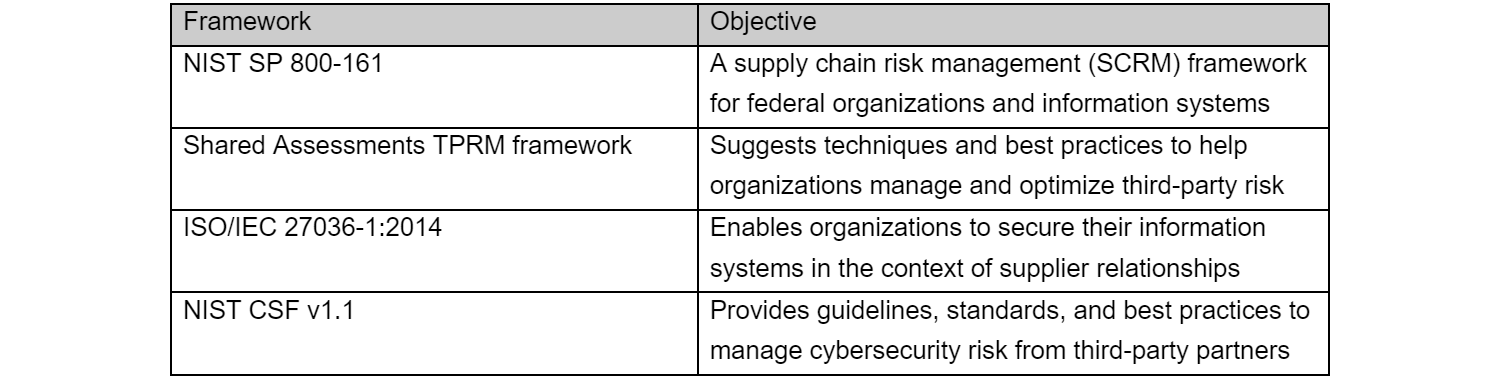
These frameworks provide a solid starting point and roadmap to set up the TPRM program. However, no single framework can identify every risk or detail every control in every organization’s particular circumstances.
That’s why companies must adapt their preferred framework to their risk ecosystem. Only then can they build a truly effective TPRM program and meet all their regulatory and risk management goals.
A Varied TPRM Solutions Market
Finally, the TPRM market itself is not one-size-fits-all. TPRM vendors specialize in different risk domains and industries. In addition, some serve customers that have a mature ERM program, while others serve companies that are just getting started.
There’s also considerable variation in the types of available TPRM solutions. Forrester categorizes these technologies into four distinct segments:
- Dedicated technologies: Provide advanced capabilities throughout the TPRM lifecycle to support organizations at any TPRM maturity level
- Exchange sponsors: Provide TPRM analytics and validated third-party assessment results
- Governance, risk, and compliance (GRC) platforms: Support TPRM and streamline additional compliance activities
- Vertical-focused vendors: Focus on specific industries with unique or complex third-party compliance requirements
To choose the best-fit TPRM solution for their needs, organizations should assess which tool can best help them identify, manage, analyze, validate, and mitigate their unique third-party risk. Vendor risk trends are dynamic and constantly evolving, so the solution should also support ongoing monitoring and reporting.
How Vendor360 Can Help You Manage Your Unique Third-party Risk
Vendor360 simplifies TPRM by automating vendor risk assessments, continuous monitoring, and internal audits. Many modern organizations with growing third-party networks are stuck with outdated, manual risk management processes that are inefficient and ineffective.
These older spreadsheet-based methods are cumbersome for aggregating third-party data. There is a high risk of details falling through the cracks in vendor onboarding and offboarding processes. Vendor360 addresses all these challenges.
This advanced and flexible TPRM platform provides enhanced third-party risk oversight. It also streamlines all TPRM tasks with quickstart templates, easy-to-use workflows, pre-populated due diligence questionnaires, and efficient issue remediation.
For a live view of Vendor360, schedule a demo.


